If you went through the previous post and got Caddy working to obtain TLS/SSL certificates on your home network you may have noticed that the process introduced some inefficiencies in the DNS lookup process. Namely, we’re now going out to a public internet DNS provider, like Cloudflare, as part of the DNS lookup process for a machine on our internal network.
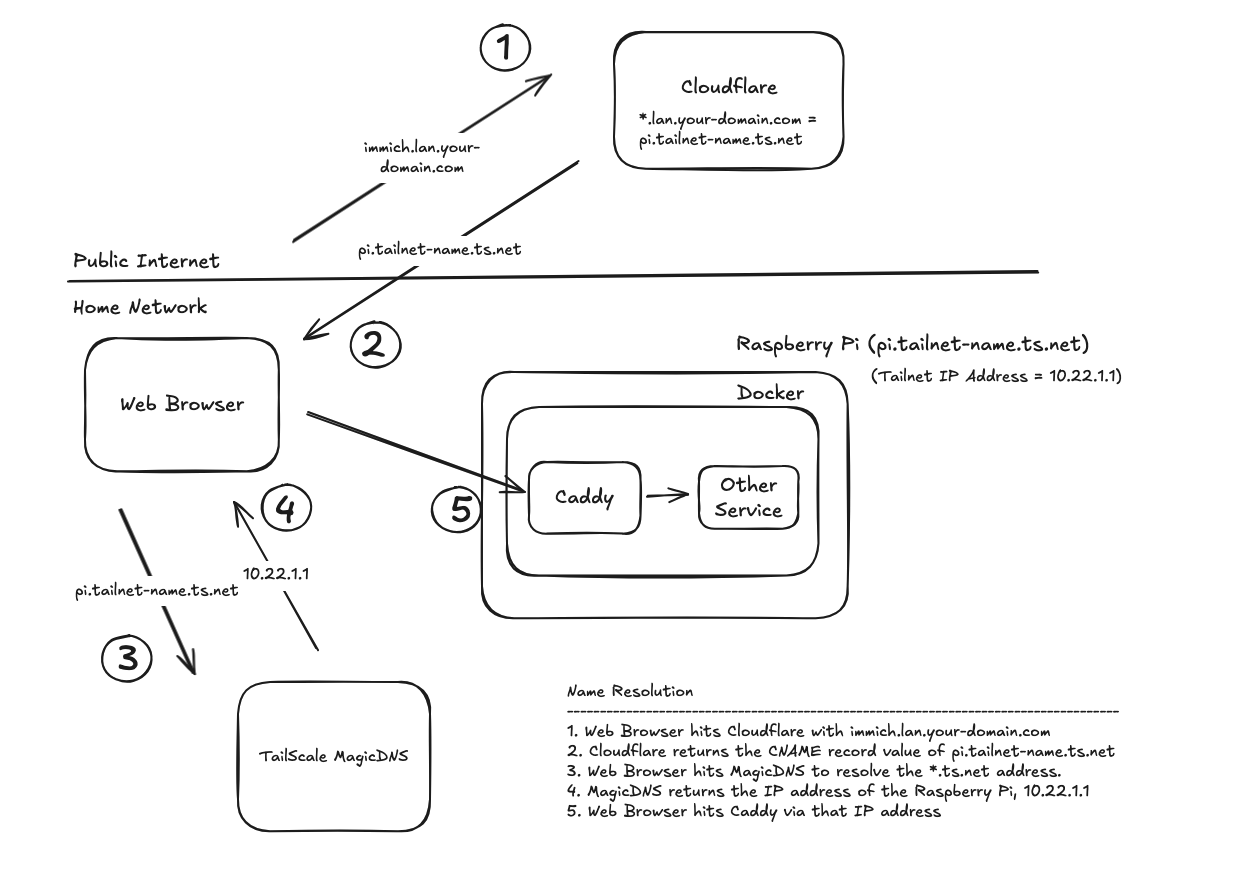
The extra time is a few dozen milliseconds, but if you want to optimize speed, you can add either AdGuard or Pi-Hole to the mix. Both products act as a middleman between your devices and the DNS providers on the public internet. Their primary purpose is to block ads by not forwarding the DNS request if the domain name of the requested address matches a know ad or malware site. However, both products also allow for DNS rewrites (DNS Records if you’re using Pi-hole), which are static mappings of domain names to IP addresses. Basically, it can resolve specific domain names to IP addresses without hitting an upstream Internet DNS service. By utilizing that feature, we’ll end up with this.
